Those who own or operate a city’s most vital assets – urban transport systems, urban water systems, urban energy systems, urban building systems – are hoping that someone will soon deliver intelligent cybersecurity relevant to the real world of cities. That means using comprehensive advanced threat protection – which, in turn, means gaining access to a portfolio of solutions and services that are integrated, pervasive, continuous and open.
A threat-centric approach to security is needed because it reduces complexity, while providing unmatched visibility, continuous control and advanced threat protection across the entire attack continuum, allowing cities (and especially those responsible for key city assets) to act smarter and more quickly -- before, during, and after an attack.
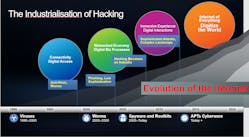
Perhaps the core security challenge facing us all today is the changing threat landscape. Agile ‘bad actors’ are increasingly better funded, and during the past few years they’ve steadily been improving their approaches – resulting in much more effective attacks. Just 10 years ago cybersecurity professionals active in this field were focused on less sophisticated attacks, like Blaster and Slammer. Many of us were receiving phishing emails from Nigeria: “If you give me $10 today, I’ll give you $1000 in two weeks.” They were often so poorly worded that we could spot them easily.
The far greater sophistication of today’s attackers makes the Nigerian scams look cute in retrospect. The name actors focus on LinkedIn, studying very detailed information about your organization, analyzing your employees, and then sending targeted emails to people, tempting them to click on a malicious link. in response, the best organizations have added many new security solutions to address these problems. But now we’re all stuck dealing with new layers of complexity.
Malicious traffic is visible on 100% of corporate networks and on 100% of government networks. There is abundant evidence that sophisticated criminals or other players have penetrated these networks and may be operating undetected over long periods of time.
In one recent review of DNS lookups originating from inside corporate networks, threat intelligence experts found that in every case, organizations showed evidence that their networks had been misused or compromised. For example, 100 percent of the business networks analyzed by Cisco had traffic going to websites that host malware, while 92 percent show traffic to webpages without content, which typically host malicious activity. Ninety-six percent of the networks reviewed showed traffic to hijacked servers.
Business and technology are both changing at an incredibly rapid pace – with all of the core elements (cloud; mobility; the explosion in applications; Big Data; IoT) each moving faster than humans can fully grasp.
All of these advances, together with changing business models, have created many new attack vectors. Each one of these vectors are being exploited by hackers.
The combination of cloud computing and mobility is a perfect storm of security threats. Experts are advising cities and utilities to prepare for these threats as if there’s a storm coming. As citizens and utilities and governments become increasingly dependent upon mobile networks, including ones which they don’t control or own, so too does sensitive data become dependent upon those same networks.
In fact, in one recent survey of experts conducted by the private firm ESG, many of the best cybersecurity professionals concluded that there are some big risks associated with the mobility which we have today, which is enabled by digitized cloud infrastructure services. On the very top of their list of risks are these four items: a lack of control; a lack of privacy; a lack of visibility; and, the inapplicability of uniform policy.
How did we get to this point of ever-increasing over-complexity? Take a moment to think back a bit, and contemplate how cybersecurity has evolved. It all began within the perimeter. If you are inside the perimeter, you are trusted. If you are outside, you are untrusted. That worked for a long time, but it’s clearly not working today -- because many people are outside the network. They are on any device, accessing any application and in many different clouds.
Information is being accessed through the data center, though public clouds, and through hybrid clouds (which help by combining elements of both the public and private). This creates what some now call the ‘Any-to-Any problem’: any user on any device, anywhere, is accessing any application at any time. A close look at the trend-lines convey one clear reality: during the next phase, things are only going to get more complicated, and more challenging.