Rapid, disruptive changes are happening in electric grids around the world. In many states and countries, initiatives are underway to integrate small renewable generation into the distribution grid to meet local demand for electricity while reducing the dependency on large central generation facilities and long-distance transmission.
This integration requires new technologies, connectivity and intelligence — all of which increase cybersecurity risks. Through its collaborative, independent research and development, the Electric Power Research Institute (EPRI) is examining the risks and exploring solutions. Connectivity and security standards, device authentication, protection of data in transit, and a basic modeling and benchmarking of risk can help utilities to plot the way to a cybersecure, integrated grid.
Security for the Multiparty Grid
Traditionally, utilities have borne the responsibility of protecting the grid from cyberattack. According to North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) standards, the mandatory cybersecurity standards for bulk power systems apply to various NERC entities — different categories of electric utilities — such as generation owners and operators, transmission owners and operators, distribution providers and balancing authorities.
The rationale behind this allocation stems from the traditional model in which most power system assets are owned and operated by utilities, which are heavily regulated by the state and federal government. Ownership over power system assets gives a utility full control over the assets and cybersecurity controls associated with them. Because a utility generates revenue through operation of the assets and has full control over them, it is logical for the utility to have responsibility for the security of the assets.
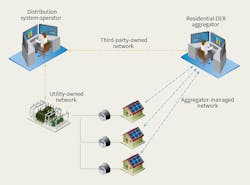
However, the electric utility industry is changing rapidly with the introduction of distributed energy resources (DERs). There are various representations of the communications channels possible when residential solar photovoltaic (PV) is in play. It is reasonable to assume solar PV and smart inverters are owned by homeowners, and a third-party aggregator manages multiple units in the neighborhood. Also assume all PV units are connected to the utility-managed distribution grid. Smart inverters give the aggregator the ability to monitor and control the operation of PVs by reading current settings and changing them.
The residential DER aggregator’s system also has a connection to the utility system operator’s distributed energy resource management system (DERMS). Based on conditions in the grid, the utility system operator can send pricing information or control signals to the aggregator, who, in turn, will take actions to meet the provisions of their agreement and maximize its profit.
In this scenario, if a critical vulnerability is found in one of the smart inverters, who should be responsible for remediation? It is likely only the manufacturer of the specific inverter can produce or update firmware to fix the vulnerability. Does the manufacturer have responsibility only to make the updated firmware available? Or, is it the manufacturer’s responsibility to find a way to deliver the new firmware to all devices deployed in the field? If so, does the manufacturer need the homeowner’s and aggregator’s agreement to update the devices?
Also assume the vulnerability is a critical one that may allow a cyberattacker to cause a malfunction of the inverter, and the malfunction of multiple inverters may impact the overall reliability of the distribution grid. Does the distribution utility need to be concerned about security updates of devices owned or managed by private businesses or homeowners? Or, is it the regulator’s responsibility to provide and enforce cybersecurity guidelines to all types of active market participants?
Answers to these questions are not easy. Moreover, this is just one security concern regarding vulnerability management and patching. There are many other security concerns, from data privacy, to protection against malware and to system security monitoring. The industry needs cybersecurity guidelines and could entertain certain levels of regulation, but any guideline needs to be based on the new paradigm of the multiparty grid, where each participant must share some responsibility for ensuring the cybersecurity for the common resource — in this case, the grid.
Device Authentication
Authentication is the process of identifying and verifying the identity of a person or a system. Although many technologies are available to do this securely, device authentication seems to be one of the major challenges in DER integration. The challenge correlates to the economics and maturity of the DER device market, rather than the availability of the technology itself. In other words, technical solutions are available, but they may be too complex or too expensive for the market.
When a system administrator provisions a communications-enabled device, a mechanism is used to identify the device when it is connecting to the network. Depending on the risks associated with the resource and the method of connection, the administrator could register the device’s unique code in a central registry, install software that generates a legitimate key for authentication, or install a hardware module that contains unique and unalterable identification properties.
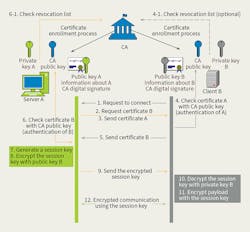
When two devices owned and provisioned by different parties need to communicate with each other, the authentication process becomes more complex. Ideally, one device can distinguish a legitimate peer from illegitimate ones, without a common registry or previously shared secret key. This scenario occurs commonly on the internet. When an internet browser connects to a web server, the browser needs a way to ensure it is connecting to the authentic website.
Transport layer security (TLS), enabled by public key infrastructure, is the most commonly used mechanism to accomplish this authentication. In this scheme, both parties trust digital certificates issued by a third-party called a certificate authority. When both devices have valid digital certificates from a trusted certificate authority, they can authenticate each other and start the communication.
There are some challenges to using certificate authority-issued digital certificates for DER systems. The first challenge is related to certificate management. Registration, renewal and revocation of certificates for multiple embedded devices from different manufacturers may turn out to be too cumbersome for a technician or electrician who manages DER devices. Although there are certificate management tools available for an enterprise information technology environment, they may not be effective for industrial embedded devices such as DERs. Lack of common operating systems and limited system resources also pose challenges for developing an effective certificate management tool for DERs or other industrial internet of things devices.
Another challenge of public key infrastructure is related to cost. Initial purchase, renewal and management overhead can put a financial burden on the DER manufacturer or managing entities, which may discourage or slow down the adoption of certificate authority-issued digital certificates and TLS.
Protection of Data in Transit
Besides device authentication, another important function of TLS is supporting data confidentiality and integrity checking. Using digital certificates exchanged during the initial device-to-device handshake, two authenticated parties can create a secure session using an agreed-on cryptographic algorithm. The challenges of encrypted communications for DER systems are like those of device authentication and mainly related to economic and ease-of-use concerns.
Limited system resources for the embedded devices are one of the main difficulties in adopting TLS, because the cryptography used in TLS requires a processing-intensive operation, especially during the initial handshakes. Increased complexity and associated costs are also common barriers to TLS adoption.
Some question the need for data encryption of DERs, claiming if the data integrity can be assured, simple exposure of data does not impact the operation. Two factors need to be considered to address this point: the relationship between data integrity and confidentiality, and the likelihood of a compromise.
Unlike smart meter data, customer privacy is less of a concern for DER data than the cyber-physical security of the device. DERs’ exposure to cyber-physical risk occurs because their settings can be changed remotely, and, if settings change erroneously, it could cause some malfunction of the devices. Therefore, an attacker can carefully plan an attack by eavesdropping and analyzing the traffic for a sufficient time. A simple one-time exposure of operational data to an unauthorized party may not matter too much, but prolonged data exposure can give malicious parties many opportunities to study and plan cyber-attacks. Encryption generally provides proactive protection against the data integrity attack by making it difficult to understand and change data.
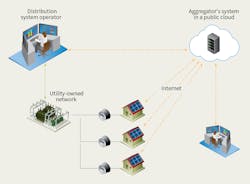
The likelihood of a compromise is positively related to the degree the signal is exposed to unauthorized parties. If a device is connected through a privately owned network with strong cybersecurity and physical security controls in place, the chance of a compromise is lower than a case where the device is connected by the internet. Because many DERs are managed by a cloud-based service, by the internet, strong encryption is an important requirement.
Cloud-Based Services
Many utility cybersecurity practitioners who are used to working with NERC CIP requirements are surprised by the prevalence of cloud-based services used in the distribution operation. Advanced metering infrastructure components, meter data management systems and DERMS are a few examples of cloud-based solutions commercially available to the distribution utilities in North America.
Over the past decade, cloud-based services have replaced information technology infrastructure steadily. However, use of cloud-based technologies in the operation of the power grid makes security practitioners uneasy, because a compromised cyber-physical system could immediately impact the safety of the public.
It would be inaccurate to say all cloud-based services are insecure, but they do introduce new and unknown risks to grid operations because they are provided through the internet — the most exposed network of all and the origin of the service could be anywhere in the world. Therefore, risk should be assessed properly, and utilities should develop mitigation strategies to keep risk at an acceptable level.
Uncertain Impact
Why does this matter? Is the risk to the grid’s reliability and safety really that great? Can risk be contained locally?
The answers are likely to change as the grid evolves. The impact of DERs to overall grid operations is a subject of active investigation by many experts. Until that information is available, it will be difficult to predict the impact a cyberattack could have on the reliability of the grid. Common sense tells us the higher the penetration of DERs, the higher the risk. Also, concentrated DER deployment in a relatively small part of a circuit may have a larger impact on the circuit and, in turn, cause instability to parts of the grid.
As DER deployment is accelerated by government mandates for renewable energy generation, utility stakeholders should take note of the need to equally accelerate the impact study of security compromise to manage the risk.
Awareness Is Key
The aforementioned cybersecurity challenges associated with DER integration are by no means exhaustive. General awareness of these risks is the first step to mitigation. The following list suggests some study areas where the industry could benefit from further research and development:
• Multiparty grid risk model in which loosely associated multiple parties are participating in the electricity market
• Framework for collaborative security management, which enables loosely associated multiple parties to work collaboratively to secure common resources
• Cybersecurity guidelines for integration for electric utilities, DER manufacturers, DER integrators and DER managers
• Lightweight encryption schemes for embedded systems with limited system resources
• Simple certificate or cryptographic key management schemes for digital certificate or key management
• Cloud security for cyber-physical systems guidelines as well as for cloud-based services in cyber-physical systems
• Grid impact studies and simulation with cyberattack scenarios, collaborative studies among electric engineers, communications specialists and cybersecurity professionals.
EPRI is working on many of these areas through collaborative research with utilities, industry, government entities and the U.S. Department of Energy, and national laboratories. EPRI’s new research and development project, ICT and Security Architecture for DER Integration, addresses some of the most pressing cybersecurity concerns related to DER integration from the utility’s perspective. ♦
Candace Suh-Lee is a senior technical leader of cybersecurity in the power delivery and utilization sector at the Electric Power Research Institute. Suh-Lee holds a MS degree in computer science from the University of Nevada, Las Vegas, and a BS degree in computer science from the University of Toronto. She has more than 15 years of experience in information and technology security in the energy sector with hands-on operational technology/information technology technical skills. Her current focus in EPRI includes security metrics, security data analytics, secure architecture for power delivery systems and situational awareness for the electric sector.
Galen Rasche is a senior program manager in the power delivery and utilization sector at the Electric Power Research Institute, where he manages the cybersecurity program. This program performs applied research in the areas of protective measures, threat management and information assurance. Rasche earned an MSEE degree from the University of Illinois at Urbana-Champaign and an MBA degree and BSEE degree from the University of Kentucky. Prior to joining EPRI, Rasche led the embedded and application security group at Southwest Research Institute, where he was the project manager for several smart grid security projects.
Check out the January 2018 issue for more articles, news and commentary.
About the Author
Candace Suh-Lee
Candace Suh-Lee is a senior technical leader of cybersecurity in the power delivery and utilization sector at the Electric Power Research Institute. Suh-Lee holds a MS degree in computer science from the University of Nevada, Las Vegas, and a BS degree in computer science from the University of Toronto. She has more than 15 years of experience in information and technology security in the energy sector with hands-on operational technology/information technology technical skills. Her current focus in EPRI includes security metrics, security data analytics, secure architecture for power delivery systems and situational awareness for the electric sector.