In the U.S., the security of the electric utility industry is guided by the North American Electric Reliability Corporation Critical Infrastructure Protection (NERC CIP) standards. NERC entities, as defined by specified real and reactive power thresholds and the performance of real-time monitoring or controlling the Bulk Electric System (BES), are required to comply with NERC CIP cybersecurity standards.
While the standards date back to 1968, a massive blackout in 2003 dictated the need for oversight, mandatory standards, and compliance. The standards have thus evolved to prescribe criteria, processes, and plans but still leave it to NERC entities how to implement these. Proof of CIP compliance is mandatory, as is passing a NERC CIP audit.
CIP standards generally don’t apply to distribution and non-BES organizations, though many non-NERC electricity organizations have chosen to adopt NERC CIP standards for various reasons. Some because they point to best practices, others because they perhaps recognize that CIP compliance will sooner or later become compulsory.
Cloud Adoption
Current NERC CIP standards do not provide for cloud concepts such as virtualization. NERC has been aware of virtualization issues for years, but adoption and implementation through revised CIP standards have yet to occur, and progress is moving forward at glacial speed, stretching into 2024 and perhaps beyond. With cloud and artificial intelligence advancing at breakneck speed, the inability of regulation to keep pace is an impediment to progress and better security for electricity utilities.
As a result, electric utilities guided by CIP are hamstrung in taking advantage of newer cloud technologies and processes that can increase security. The NERC Standards Drafting Team is currently reviewing CIP Virtualization standards with cloud accommodation of BES cyber assets to address:
⦁ Sharing of hardware resources
⦁ Isolation/access of the Management interface
⦁ Identification and categorization of cyber assets.
With CIP standards eventually embracing the cloud, cloud service providers such as Microsoft Azure and AWS already have use cases. Azure Government is a US government cloud environment segmented from the Azure cloud and provides additional and granular access protocols. However, cloud environments operate under a model in which responsibility is divided between the cloud service provider and the customer. For instance, AWS manages controls for the cloud infrastructure, but tenant organizations are responsible for ensuring compliance with CIP requirements. Both tenant organizations and cloud service providers perform security control activities. Consequently, it’s critically important for electricity organizations embracing cloud environments to understand their obligations clearly. Organizations with cloud roadmaps should have their environments fully architected, security enabled, and data flows documented.
Target State
Since NERC entities are responsible for implementing CIP standards, processes, and plans, “Target State” helps frame these activities. A “target state” might be considered a destination, and the implementation of standards is the journey. The target state is shaped by organizational goals and risk appetite. Thus, the level of security and how much is enough differ for each organization.
Depending on the target state destination and the speed of travel, the journey is also different for each organization. Nonetheless, all electricity organizations share an overarching security goal appropriate to the threat landscape.
Maturity evaluations help measure progress toward a desired target state. Models and frameworks such as the Cybersecurity Capability Maturity Model (C2M2) and the Capability Maturity Model Integration (CMMI) enable organizations to evaluate their cybersecurity implementation and set goals and priorities for improvement. The models employ rating scales to reflect maturity. For instance, C2M2 employs a scale of 0-3, while NIST CSF (National Institute of Standards and Technology Cybersecurity Framework) uses four implementation tiers. NIST Tier 3 (Repeatable) is the minimum level most organizations should achieve. Highly mature organizations, those typically operating at Tier 4 (Adaptive), employ controls and processes that are more comprehensively implemented, risk-based, and quantitatively understood.
Some organizations have combined the CMMI with the NIST-CSF framework that examines People, Process, Technology, and Scope (PPTS) and helps IT and OT managers detail roadmaps to attain the desired target state.
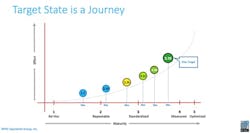
Using the hybrid CMMI-NIST CSF maturity model with a scoring scale of 1-5, utilities and organizations, which typically have a high security and regulatory burden, run between a high 3 to a low 4 maturity scoring. Advancing up on the maturity scale is not an equal journey. The level of effort required becomes incrementally more difficult the more mature an organization becomes. As shown in Figure 1, moving from 1 to 2 takes less effort than moving from 2 to 3.
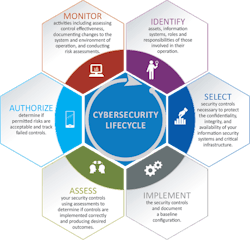
A cybersecurity lifecycle approach that is structured, grounded in best practices, and yet flexible is vital to chart journeys to the target state. The cybersecurity lifecycle and its stages apply universally to all IT and OT environments, as shown in Figure 2.
Closing Thoughts
Does a 4.5 maturity score give you better security than a 3.5? The answer is not clear. Higher scores reflect improved capabilities and, as a result, lower the risk of cyber attacks, but a low probability does not guarantee there won’t be an attack.
Yet, insurance companies look at the maturity of cybersecurity controls to determine insurance premiums. Ratings agencies such as S&P, Moody’s, and Fitch also factor in the maturity of cybersecurity controls to assess credit risks of bonds issued by local governments to finance capital projects, such as utility expansions. The higher the rating grade, the less risk to investors and the lower the interest rate. Conversely, consider the impact of downgrading a credit rating due to weakness in cybersecurity - this could cost local government millions of dollars in additional interest payments. Given those potential costs and the fact that the NERC Critical Infrastructure Protection standards are mandatory for NERC registered entities but universally applicable to the remainder and the very real cybersecurity threat, it is clear that choosing the right guide is key to safely reaching the journey's end.
About the Author
Jeffery Mayger
Jeffery Mayger is Senior Director, Cybersecurity Solutions, at PSC Consulting.