Cybersecurity for Distributed Energy Resources and SCADA Systems
As the U.S. bulk power system continues to focus on distributed energy resources (DERs) for more of our overall electricity needs, the ability of the grid operators, power marketers, and reliability coordinators to maintain a secure supply will be increasingly challenged. This document reviews the various DER sources and the challenges in maintaining cybersecurity situational awareness and a stable risk profile.
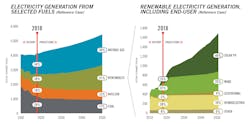
Power Generation — What Will it Look Like in 2050
The U.S. Energy Information Administration1 has projected a continuous increase of power generation from renewables and a decrease of the same from coal and nuclear. As the economics of generation continue to change, these projections may become even more pronounced.
Correspondingly, the number of renewable generation locations required to achieve these projections will increase significantly. The power density of solar photovoltaics (PV) and wind is much lower than fossil fuels or even hydroelectric. The National Renewable Energy Laboratory (NREL)2 studied the density of solar PV of various designs in 2013. There are many factors involved including types of collectors, fixed versus axis tracking, and others, but the overall power density average is between 6 to 8 acres of land per megawatt of ac power generated. Wind requires even more land, with the NREL estimating 12 to 56 hectares per megawatt for an average wind farm with modern generators.3 While this density will improve with better technology, there is no doubt that the number of physical installations required to increase the amount of renewable energy on the grid will need to be significantly higher in 2050.
Increased Attack Surface
The increase in the number of physical installations means a corresponding increase in the number of supervisory control and data acquisition (SCADA) systems required to manage and control the generation and interconnection of these generation systems. With the higher number of interconnections, there is a related increase in complexity of the overall grid control system. These unavoidable trends of higher number of generation systems and increased complexity of control systems result in higher cybersecurity risk across the board for renewables and the need for a strategic approach for management of renewable facilities across the nation.4
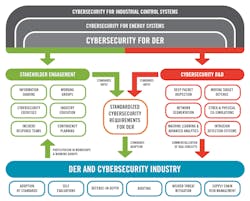
The SCADA system market has many different components and vendors involved in many different applications, even within the electric power delivery market. Therefore, developing a management approach that has a common architecture and approach is difficult. There are no software application packages available that universally support all the management and operational requirements across the SCADA system market. Electric utility owners and operators will need to develop a SCADA management architecture and roadmap that focuses on the ability to scale in size and stay efficient, as well as develop a suite of applications to meet the operational and security requirements. Figure 2 is based on a report5 from Sandia National Laboratories issued in December 2017.
Multiple Stakeholders and Administrators – Who’s Accessing the SCADA System?
As the number of DER installations increases, so does the number of organizations and personnel involved in managing the systems. How does the industry manage the risk of an increasing workforce that requires ever-sophisticated training to address not only the technology and growing complexity of the interconnected grid, but also the increasing dynamic threat from ransomware, nation-state attacks, and other cybersecurity threats?
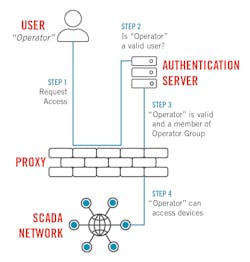
One security control that can provide risk reduction and benefits tremendously from a centralized service approach is electronic access control. Most SCADA devices now support some form of authentication service, such as Remote Authentication Dial-In User Service (RADIUS), Lightweight Directory Access Protocol (LDAP), or Active Directory (AD), and for those devices that do not, there are authentication proxy devices that can enable this functionality.
The security benefits include the ability to update user information across all devices with a few commands, implement role-based access control with appropriate privileges for each device, and the associated accounting, logging, and audit trails that are maintained with the centralized service. Of course, if the centralized service is not available because of communications or network issues, especially in remote locations, dispatching an engineer or technician to perform local actions and/or fix the communications issues is required to repair and maintain control.
Supply Chain — How Diverse are DER Control Systems?
An article in IEEE Spectrum showed how a single utility and vendor can reprogram many microinverters in a single day6 to meet growing needs for customers. This is an incredible accomplishment that demonstrates the ability of distributed systems to scale across an entire service area. However, it also indicates that a malicious cyberattack may be able to use the same technology and access to cause an outage or, even worse, damage a large amount of equipment.
The strategic roadmap and architecture need to include multiple solutions for operations and management of DER systems to ensure that one authorized party, regardless of how trustworthy it may be, does not have the authority to impact widespread segments of the power grid.
Operational Awareness — Is This Normal or Not?
As the modern electric grid grows more complex, the ability for utility operations staff to determine the difference between a normal operational activity and a malicious intruder or attack becomes more difficult. In August 2019, the United Kingdom "suffered a power outage that affected more than 800,000 customers."7 The utility said it was certain that the power failure had not been the result of malicious action or a cyberattack. The British regulator demanded an investigation to conclusively determine the cause of the outage. Considering that minimal cybersecurity forensics are in place and the number of interconnections in the U.K. grid, dismissing a cybersecurity event as the cause so early into the investigation is questionable.
With even more external organizations being connected and involved in DER operations in the future, it will become increasingly difficult to determine the cause of future incidents.
Confidentiality and Trust
The common triad of principles for a secure system is defined as confidentiality, integrity, and availability (CIA). In traditional SCADA systems, availability, and integrity are always a higher priority than confidentiality. However, with DER and many different parties engaged in the overall process of generating and distributing electricity, including residential consumers, the need for confidentiality and, perhaps more importantly, an enabling technology for transactive energy — starts to become more important.
The primary way to achieve confidentiality for information is to use encryption at rest and during transit. Since most current SCADA systems are contained to internal networks and are primarily used to transfer device status information to a central energy management system, the information traveling across the network isn’t very interesting to typical intruders and is rarely encrypted. However, as we have more distributed SCADA systems using several communication methods from a wide variety of service providers, the need to include more sensitive information along with typical SCADA data points is becoming more common.8
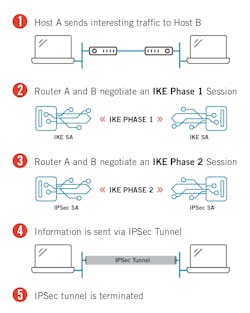
There are several different ways to protect this information, including traditional virtual private networks (VPNs) between facilities that rely on digital certificates for authentication, and new technologies such as blockchain that may enable a whole new way to trade energy directly between participants.10 All these mechanisms need an underlying trust model that satisfies all engaged parties that the information is protected — VPNs use X.509 certificates while blockchain uses the digital public ledger that gives the technology its name. In any case, confidentiality and the various technologies used to implement it will be critical to enable the potential of DER in supplying majority of the electricity on the grid by 2050.11
Summary
DER installation will increase in number and complexity, replacing more coal and nuclear plants as they age and are decommissioned. There are several areas in cybersecurity that require attention as this transition moves forward:
- Developing a strategic roadmap and architecture that scales to meet the anticipated growth will provide a method to manage cybersecurity risks.
- Controlling who has access to DER SCADA systems and what level of privilege each role of users has provides accountability and audit trails needed for effective cybersecurity risk management.
- Ensuring multiple vendors are qualified to compete in the DER SCADA market will provide diversity in the supply chain and ensure that a single entity does not have enough privilege to cause a widespread DER outage.
- Training staff to recognize the differences between issues caused by the operational environment rather than malicious actors will help prevent additional investigations by regulators and increase the level of trust that customers have in the utilities.
- Maintaining confidentiality of information will become more important as the move to transactive energy becomes the normal way of doing business with DER stakeholders.
References
[1] "Annual Energy Outlook 2019 with projections to 2050," U.S. Energy Information Administration, Jan. 24, 2019, https://www.eia.gov/outlooks/aeo/pdf/aeo2019.pdf
[2] "Land-Use Requirements for Solar Power Plants in the United States," National Renewable Energy Laboratory, June 2013, https://www.nrel.gov/docs/fy13osti/56290.pdf
[3] "Land-Use Requirements of Modern Wind Power Plants in the United States," August 2009, https://www.nrel.gov/docs/fy09osti/45834.pdf
[4] Department of Energy, Quadrennial Energy Review (QER), "Transforming the Nation’s Electricity System, Chapter 4," Jan. 6, 2017, https://www.energy.gov/sites/prod/files/2017/02/f34/Chapter%20IV--Ensuring%20Electricity%20System%20Reliability%2C%20Security%2C%20and%20Resilience.pdf
[5] Lai, Christine; Jacobs, Nicolas; Hossain-McKenzie, Shamina; Carter, Cedric; Cordiero, Patricia; Onunkwo, Ifeoma; Johnson, Jay, "Cyber Security Primer for DER Vendors, Aggregators, and Grid Operators," Sandia National Laboratories, December 2017, https://www.researchgate.net/publication/322568288
[6] Fairley, Peter, "800,000 Microinverters Remotely Retrofitted on Oahu — in One Day," Feb. 5, 2015, https://spectrum.ieee.org/energywise/green-tech/solar/in-one-day-800000-microinverters-remotely-retrofitted-on-oahu
[7] Weiss, Joseph, "We can’t detect a cyberattack that trips a plant, but we immediately identify an outage as not being a cyberattack?," Aug. 12. 2019, https://www.controlglobal.com/blogs/unfettered/we-cant-detect-a-cyber-attack-that-trips-a-plant-but-we-immediately-identify-an-outage-as-not-being-a-cyber-attack/
[8] Nguyen, Hieu Trung; Battula, Swathi; Takkala, Rohit Reddy; Wang, Zhaoyu; and Tesfatsion, Leigh, "Transactive Energy Design for Integrated Transmission and Distribution Systems" (2018). Economics Working Papers: Department of Economics, Iowa State University. 18004. https://lib.dr.iastate.edu/econ_workingpapers/41
[9] Mason, Andrew, "IPSec Overview Part Four: Internet Key Exchange," February 2002, http://www.ciscopress.com/articles/article.asp?p=25474&seqNum=7
[10] "Trading Energy: Will Blockchain disrupt the energy industry?," March 26, 2019, https://hackernoon.com/trading-energy-will-blockchain-disrupt-the-energy-industry-34a6a9e90112
[11] Qi, Junjian & Hahn, Adam & Lu, Xiaonan & Wang, Jianhui & Liu, Chen-Ching. (2016). Cybersecurity for Distributed Energy Resources and Smart Inverters. IET Cyber-Physical Systems: Theory & Applications, https://digital-library.theiet.org/content/journals/iet-cps/1/1
About the Author
Jeff Pack
Jeff Pack specializes in cybersecurity services for POWER Engineers, Inc. He has over 31 years of experience in electric utilities, energy research and development, and information security solutions. He is an experienced leader and subject matter expert in the cybersecurity field, including program development, consulting, and operations. Jeff has also provided executive and team leadership for numerous projects related to cybersecurity and operations. He has bachelor’s degrees in engineering and computer science from Montana Tech and an MBA from Boise State University.