Improving Cybersecurity: Communication Gateways for Substations
The significant surge in distributed energy resources (DERs) and energy storage systems (ESS), together with the upward trend of unmanned substations, power systems have become more complex. Therefore, digital substations play an increasing and important role in transmission systems providing both stability and flexibility to power supplies. However, upgrading existing substations to digital substations is not straightforward due to the investment required to retrofit the large number of serial-based legacy devices.
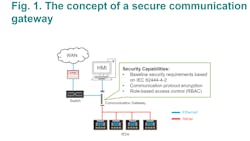
Communications gateways can help to overcome this problem as they help serial-based legacy intelligence electronic devices (IEDs) communicate with ethernet-based networks; they are also a cost-effective solution. With the serial-to-ethernet problem solved, however further issues can arise, namely cyberattacks that always pose huge threats to Ethernet-based networks creating the issue of cybersecurity in upgrading substations at the forefront.
In substation upgrading projects, communication gateways act as data concentrators managing the large numbers of legacy IEDs but these communication gateways rarely incorporate adequate security measures. Therefore, a high risk exists that malicious actors can easily access legacy IEDs through these gateways to cause power outages, damage critical equipment, endanger people’s lives and cause huge financial losses.
With numerous cyberattacks on critical infrastructures during the last few years, the necessity of enhanced cybersecurity is now being recognized worldwide. For example, there was a security breach of the transmission system energy in Los Angeles County and Salt Lake County in March, 2019 due to identified vulnerability issues.
The Solution
There is no single silver bullet solution available for cybersecurity as it relies heavily on a Defense in Depth (DiD) approach. In upgraded substations, cost-effective communication gateways are the norm to connect large legacy IEDs to the operating system. Therefore, the communication gateways installed should provide full secure defense capabilities to prevent any cyberattacks, but this is not so straightforward when considering the current solutions available in the market.
To protect communication gateways from these cyberattacks it requires the integration this of three technologies:
- Baseline security requirements
- Communication protocol encryption
- Role-based access control (RBAC)
Baseline Security Requirements
The security capabilities of communication gateways are a minimum requirement. It is important to note that network devices are accessed frequently for configuration settings and health status monitoring during installation, maintenance and data transmissions. The general industrial security guideline, IEC 62443-4-2, is a baseline requirement for network components, such as communication gateways, which will help to secure the infrastructure of a network and provide a solid foundation for network development and expansion.
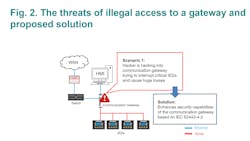
It is important to first understand the hackers’ motives and their attack methods in their mission to disrupt critical network devices and cause huge losses. The common cyberattack methods employed are as follows:
- Password cracking (e.g.: 1~1000000000000, A~ZZZZZZZZZZZZZ).
- Sniffer and data breaches in unsecure areas.
- Configuration File and Program Tampering.Hacking.
- Distributed Denial of Service (DDoS) attacks.
- Identity theft.
Password cracking -alternatively known as a brute-force attack is very common. Basically, hackers try various combinations of passwords again and again until they are successful. Therefore, to prevent password cracking, gateways must integrate password policies that enforce the following:
- The default password warning for first-time login must effectively inform users to change their password to increase network security.
- The password composition must state what types of characters are allowed, as well as the number of characters required before a password will be accepted as valid.
- The password needs to be changed at regular intervals and only allow limited retries in case of password failure.
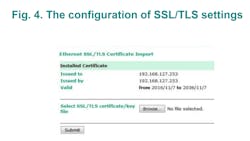
Sniffer and Data Breach Prevention — Transmission of unencrypted packets will most definitely reveal critical information that includes the commands to configure devices, commands to monitor device status and logs. Hence, communication gateways should secure connections by some methods such as Transport Layer Security (TLS) which is a popular cryptographic protocol designed to provide communication security over the network.
Configuration File and Program Tampering Resistance — If the hacker is able to snatch the plain text configuration files of a communication gateway, they can easily modify them and import the modified configuration files to the hacked communication gateway. Because of the incorrect configuration, the gateway may act abnormal or behave unpredictable, placing substation operations in danger.
To prevent the tampering of configuration files or programs, communication gateways need to encrypt configuration files and programs in order to make it difficult for hackers to modify them. Each manufacturer should have their own way of encryption. For example, a gateway can configure and store the pre-shared key (PSK) in the gateway. When doing configuration file export or import, the configuration file will be encrypted or unencrypted by the PSK.
Distributed Denial of Service (DDoS) is a strange phenomenon because malicious actors usually use malware that does not really damage the communication gateway. Instead, it is a cyberattack where the malicious parties seek to make a resource (service) of the gateway unavailable. There are two main forms of DDoS attacks:
- Traffic attacks mainly on a network’s bandwidth whereby, a large number of attack packets cause the network bandwidth to be blocked.
- Attacks on resources mainly directed at the gateway, e.g., the host's memory is exhausted or the CPU is occupied by the kernel. Malware through a large number of normal packages results in a failure to provide the gateway services.
To prevent DDoS attacks on the gateway, it is preferable for the gateway to have built-in features to drop suspicious packets on detection.
Account and Identifier Management – Any component of a network should create account and identifier management that identify individuals by user, group, and services. This stops users accessing devices on the network for which they have no permission, so those users with different roles on a network have different privileges.
Communication Protocol Encryption
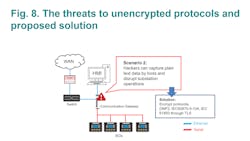
In substations, IEDs are managed or controlled by using communication protocols such as IEC 61850, DNP3, IEC 60870-5-104, or Modbus. If these protocols are unencrypted, networks would be vulnerable to cyberattacks as hackers can get critical data from monitoring data packets. Therefore, the primary goal of protocol encryption is to provide a secure communication channel between two network devices.
The common threats to unencrypted communication protocols occur when data is exchanged between network devices as malicious actors will have easy access to view the exchanged information. Hence, if it is critical information, substation operations can be in danger. The common threats are listed below.
- Hackers can figure out how to establish connections to a network device, monitor power quality, and even control I/O status. This will allow them to access the communication gateway to do whatever they wish.
- Hackers are able to eavesdrop and alter the packets. They can then send the tampered packets back to the communication gateway to wreak havoc.
Developed in 1994, TLS is a technology that can be used to encrypt communication protocols. It has had in-depth penetration testing for decades, involving many revisions and a number of installation bases consisting of millions of users. IEC 61850, IEC 60870-5-104, DNP3 are Ethernet-based protocols. With regards to cryptography, symmetric and asymmetric methods are used in TLS simultaneously as performance and security and are therefore important factors when transmitting data. The version of TLS v1.2 or above is recommended by IEC 62351-3.
Role-based Access Control (RBAC) to prevent Assets Mis-Operation
The network must be able to identify and authenticate all users, including humans, processes, and devices. This allows separation of duties and the principle of least privileges to ensure every user only has access to information and devices that are essential to perform their designated role within the network. At this stage, it is important to note that incorrect commands are often executed by engineers who are not familiar with power systems, consequently destabilizing the power system and putting it at risk.
- Threats to Non-RBAC Mechanism - If the substation system is without an RBAC mechanism, this can create problems and threats as follows:
- The employees responsible for remote terminal unit (RTU) maintenance, their job function requires them to remotely view the working status of the substation, but not to control the RTU.
- The privilege level for more senior employees must be adjusted accordingly if their job function requires more access to devices and applications.
- When employees leave an organization, they should no longer be able to access the network and must immediately surrender their network privileges.
Therefore, RBAC built into a communication gateway is really valuable having the potential to reduce complexity, the possibility of asset mis-operation and the costs of security administration in networks.
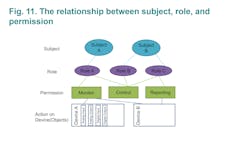
RBAC in Power Systems - defines subjects, roles, and permission:
- Subjects indicate users, automated systems, and software applications. For example, a power management system, a supervisory control and data acquisition (SCADA) system, and a power dispatch application in the energy management system (EMS).
- Roles are related to job functions e.g. include a distributed system operator, IED maintenance, etc.
- Permission indicates the action that is assigned to a specific device.
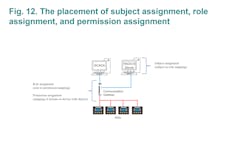
The RBAC Assignment of a Communication Gateway
A communication gateway is mainly used to convert one protocol to another. For substation automation, data is quite important for management, especially for control commands. Therefore, the communication gateway should focus on the right of data access control. Based on the standard of IEC 62351-8, it defines the permission, roles, and role-to-permission assignment. Especially for the permission (action-to-object) definition, “each object” can be configured to perform actions.
Communication gateways perform protocol communication related to devices with objects. Typically, a gateway will contain hundreds or even thousands of objects. Therefore, the standard definition for a gateway might be off the mark as gateway configuration has become more complex. In order to use a gateway easily, one design concept is described below:
Role Assignment (Role-to-Permission Mapping): a user can create roles as defined by the user, and then configure permissions for the created roles. For communication gateway design, three options can be selected:
Monitor: this role can monitor data through read commands.
Control: this role can execute control commands.
Reporting: this role can receive spontaneous commands when a data event is triggered.
Permission Assignment (Action-to-Device Mapping): In substation automation, a communication gateway will connect several legacy devices. For example, it should define the mapping between the action and device. This is a little different from IEC 62351-8, because the Standard defines action-to-objects that are from a device’s viewpoint.
Summary
For substation operations without the threat of cyberattacks, the cybersecurity within networks and devices are essential. To eliminate the risk, a three-pronged approach, which entails baseline security requirements for communication gateways, communication protocol encryption, and role-based access control (RBAC), is recommended to provide secure communication gateways in networks.
Using network devices equipped with basic security capabilities and that are IEC 62443-4-2 compliant is an effective precautionary measure to ward off cyberattacks. These basic security capabilities should include password cracking defense, sniffer and data breach prevention, tamper-resistant configuration files or programs, DDoS defense and the account and identifier management.
Networks are especially vulnerable to cyberattacks if data from Ethernet-based communications protocols are unencrypted. Once hackers have invaded a substation’s network, they can easily capture data and learn a lot about a network’s communication behavior. They can easily cause havoc by sending a misleading command to control an IED. To counteract these types of malicious activities, communication gateways should employ encryption communication protocols.
With regards to the mis-operation of assets, role-based access control (RBAC) is the ideal model to address this issue, especially in complex systems. Most incidents of mis-operation occur when engineers have access to information or sections of a network that do not pertain to their job function, creating a scenario for mishaps. More importantly, whether employees are promoted or resign, their privilege level must be reviewed, adjusted or revoked. Thus, network access should be based on the roles of individual users within the network, and the communication gateways should be capable of assigning the necessary permission for access to the different role players.
About the Author
Sean YH Wang
Sean YH Wang has a Master’s Degree from the Graduate Institute of Electronic Engineering, National Taiwan University. and has eight years of experience as a solution provider in the power industry. He is the business development manager in the Moxa Vertical Business Unit that focusses on communication systems for substation automation and renewable energy. In the company, Wang is responsible for collaborating with Moxa’s product team in developing communication solutions for power systems and developing power business strategy with the sales organization.