Since the terrorist attacks of Sept. 11, 2001, America has become keenly aware, and rightly so, of imagining what form another attack would take. For the utility industry, the focus of most news media attention has been grand-scale attacks on the power grid, be they cyberattacks to bring down large sections of the grid, electromagnetic pulse attacks to destroy the grid or attacks on individual power stations, like the rifle assault on Pacific Gas and Electric Co.’s Metcalf substation in the San Francisco Bay area.
Lost in all this attention and media coverage is something perhaps more acute, urgent and frequent — attacks on utilities’ infrastructure motivated by theft and vandalism. These attacks cause more than power outages. They compromise safety by creating hazards to employees and the public. They degrade reliability in terms of a utility’s power system integrity and availability, which, in turn, harms a utility’s brand, hard-earned reputation and confidence of its customers. These types of attacks impact revenue because of service disruptions and costs to repair damages. The attacks also invite scrutiny by government agencies in the compliance realm, which could lead to penalties, sanctions and more negative publicity for not meeting regulatory requirements.
The Scope
The electric utility industry’s main goal every day is to keep the lights on, but the target for wrongdoing is large and widespread. Prevention of physical attacks and cyberattacks on the grid is, and should be, the highest priority. There are more than 400,000 circuit miles (643,738 km) of transmission and more than 45,000 substations in the United States, so utilities must direct and align limited resources according to the greatest risks.
The electric utility industry is the only critical infrastructure sector — of 16 major sectors, including telecommunications, water and transportation — that is subject to mandatory federal reliability and cybersecurity standards. Electric utilities must continuously invest in security measures that protect the grid against evolving threats.
Electric utilities must use sophisticated techniques to allow the grid to recover quickly should an attack occur. They also must constantly plan for emergency situations that threaten the reliability of the grid, and take steps to identify potential threats and methods to defend against them. This is obviously crucial in the cybersecurity realm, and those threats are constantly changing and evolving.
To accomplish this, the industry must strengthen the grid; continually assess threats; prioritize resources and collaborate with government agencies, especially law enforcement; share information; provide tours and access to facilities; and offer training to police and investigators, if necessary.
The Threats
Who are the perpetrators? They could be thieves who seek to steal copper, they could be vandals, they could be angry customers or even angry employees. They could even be violent radicals, extremists and terrorists. While the threats and attackers are many, the goal is singular: keep the threat away from the electrical system. It is a simple answer but one that demands a very comprehensive solution.
What is needed? Like any adversarial situation, a utility must know the enemy’s knowledge of the intended target, the enemy’s capability to attempt the attack and the enemy’s intent to conduct the attack. Fleshing this out requires resources, intelligence, awareness, readiness and coordination. Thwarting an attack involves deterring it in the first place, detecting when a breach is occurring and assessing it, and delaying the attack to allow time to defend against it, while communicating effectively to be able to respond appropriately.
SMUD: A Case Study
The Sacramento Municipal Utility District (SMUD) is the sixth-largest customer-owned utility in the United States. Its more than 2,000 employees serve about 1.4 million people in a 900-sq mile (2,331-sq km) area. A few years ago, intrusions at SMUD facilities and the theft of copper were on the rise. For example, 2010 saw 56 facility intrusions and 52 incidents of copper theft. A year later, in 2011, facility intrusions spiked to 83 incidents and copper thefts rose to 57. This trend was disturbing.
In 2012, SMUD embarked on implementing a set of solutions that resulted in a precipitous drop in facility intrusions and copper theft incidents in just two years. In 2014, the number of facility intrusions dropped tenfold to just eight, and the number of copper thefts dropped almost twentyfold to just three. These striking decreases resulted from several key efforts and some fortunate circumstances:
- Enhancing security at many of the most historically targeted distribution and transmission substations
- Providing hardened perimeter fencing using high-tensile mesh
- Increasing video monitoring and reporting, including wireless video intrusion detection systems that provide excellent deterrence and detection
- Enhancing the security approach to escalation, changing from observe and report to observe, assess and intervene, as appropriate
- Continuing to provide a community outreach program, especially at neighborhood watch meetings, where the community is asked to report suspicious activity directly to law enforcement or SMUD
- Continuing to partner with the local law enforcement’s metal theft task force, resulting in communication and coordination with other utility agencies
- Increasing compliance inspections by county law enforcement at recycling centers.
Each of these measures resulted not only in the dramatic drop in incidents but also in arrests. While it should be mentioned that copper theft is somewhat dependent on the price of copper, it is only part of the story about what motivates facility intrusions. The other threats remain, and utilities must remain vigilant and proactive.
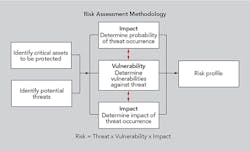
Prioritizing through a thorough risk assessment can help to determine the threat and vulnerability of particular facilities and the necessary scope of escalated security at substations and transmission and distribution facilities. The assessment should consider response plans, event analysis, and maintenance and testing.
Following are some tools to help conduct the audit:
- CARVER (criticality, accessibility, recuperability, vulnerability, effect and recognizability) matrix
- ECIP/ITS (enhanced critical infrastructure protection infrastructure survey) tool from the U.S. Department of Homeland Security
- THIRA (threat hazard identification and risk assessment)
- Attack tree modeling.
Deterrence
The electricity sector is comprised of a lot of infrastructure spread over large areas. Critical and expensive facilities are located in areas as diverse as densely-populated and heavily-concentrated neighborhoods as well as wide, vast, rural and sparsely-populated countryside. Protecting facilities like substations, transmission and distribution equipment by their very nature is far more challenging than protecting corporate offices, warehouses and generation stations. Security presence, sometimes even armed, at the latter is far more common and practical than at the former.
These can range from passive measures — like clearly understandable signage to warn intruders; perimeter barriers like high-tensile mesh fencing; and security lighting that can be complemented with clear zones to leave the attacker with no place to hide — to more active measures like establishing a security personnel presence be it fixed or random.
All measures, though, need to be built on and around a strong foundation of intelligence measures designed to collect, process, analyze, evaluate and interpret information about potential threats. Critical intelligence is developed and used by working closely and in tandem with local law enforcement and state and federal agencies. Intelligence is also developed by monitoring social media as well as relevant local, regional, national and even international news media, and by connecting with the local community through neighborhood association and watch groups and even door-to-door grassroots communication.
Detect and Delay
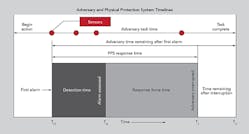
Dispersed facilities over large areas demand physical security measures be installed to detect intrusions. These physical security measures consist of perimeter alarms and motion-detection technology, which are relatively inexpensive and provide local or remote alerts a breach either is occurring or could occur soon. Physical security measures include video technology that, in recent years, has become very affordable as cameras have become cheaper and wireless, easy to install and network-connected by fiber, microwave, modem or cellular web-based communications.
Physical security measures allow security personnel to monitor and assess the potential threat and evaluate its legitimacy, determine if it is valid and begin to respond.
Geography and traffic will impact response time, so it is critical to consider installing additional security measures to slow down the intruder’s breach, handiwork and eventual flight from the scene. As previously mentioned, better fencing is key and has worked very well for SMUD. Considering the use of block walls, gates, crash-resistant protective bollards and hardened locks as measures, individually or in tandem, can hamper an intruder long enough to get security or law enforcement personnel on scene to thwart the attack and even make an arrest.
Respond
The response plan can consider a wide-ranging scope of tactics and measures including even potentially controversial possibilities like armed drones. Some may consider that approach to be extreme, but weighing the value of the target and the capability and intention of the attack, all options should be considered, especially if the attackers, or their motives, are potentially extreme.
In developing a response plan, these are some questions to ponder:
- Are the systems in place redundant?
- Will physical controls enable an attack intervention or merely forensic evidence collection?
- Are sensor and barriers complementary?
- Who will respond? Security, local law enforcement agencies or operations personnel?
- Here is something to consider: How long the attack can be delayed versus the time it takes to respond will determine success. If the delay is 15 minutes and the response time another 30 minutes, the odds of success are fleeting.
What Is Next?
Protecting against any threat — from the inexperienced criminal fumbling through a copper theft, to a vandal seeking revenge on his utility (or employer), to a well-coordinated attack carried out by violent extremists or terrorists — is going to be resource intensive. All employees must report peculiar activity they see, hear about or read on social media.
Regardless, it is better to have a plan and not need one than to need a plan and not have one. And remember, physical security best practices provide the foundation for meeting regulatory compliance.
James Day ([email protected]) is the program manager for physical security at the Sacramento Municipal Utility District. Day has been at SMUD since 1997 in a number of security roles. He has more than 38 years of experience in the security field. He brings a wealth of experience from the military, private industry and public utility sectors.