In the song “Strawberry Fields Forever,” John Lennon sings, “Living is easy with eyes closed.” That may have been true in Lennon’s world, but for CenterPoint Energy Houston Electric (CEHE), living — and conducting daily operations — is far easier with eyes wide open.
Among the challenges electric utilities face, theft by diversion and meter tampering have a huge impact every year. This affects ratepayers and investors; thus, the utility has a responsibility to have an active theft-detection program. The Public Utility Commission of Texas requires all electric utilities in the state to maintain active theft-detection programs (Substantive Rule 25.126).
CEHE takes this responsibility very seriously. A major weapon in its arsenal is analytics.
Success Factors
The goal of a theft-detection program is to protect a utility’s revenue stream. In addition, it must be accomplished in a cost-effective manner. CEHE measures success in a variety of ways:
- Dollar amounts billed
- Labor and material dollars billed
- Prevented losses
- Number of field investigations as a factor of the number of diversions/meter tampering found
- Cost of the program compared with the dollar-value impact to revenue stream.
Each year, U.S. utilities estimate electricity theft alone costs the industry more than $1 billion in revenue. The utility industry is adapting to the use of analytics in several important areas, including theft detection. CEHE has had a theft-detection program for many decades, but the analytics were basic up until recent years. However, once CEHE implemented its advanced metering system, the utility quickly realized the tremendous amount of data, if correlated correctly, could identify the premises where suspected theft was taking place.
From Data to Work Orders
CEHE began the work of taking all that data — approximately 220 million elements every day from a region covering more than 5,000 sq miles (12,950 sq km) — and developing a way to process it into field orders for investigation as well as metrics to determine how well the program is doing. When the algorithms were developed, it was obvious the ability to correlate events in the field led to greater accuracy. The algorithms used and assumptions made are continually refined as the utility gains a better understanding of the data.
The data must be filtered to ensure a field crew is not on-site during the time of a meter alert. CEHE also has advised electricians to notify the utility before they pull meters to rewire or make repairs. If an electrician pulls a meter without that notification, the analytic system will issue a work order to investigate for meter tampering. Many times, a CEHE crew will arrive at the property before the electrician has finished the repair work.
Work order system improvements have contributed to improved data gathering during the field investigation process. Regulations require records of evidence, including multiple photographs taken at the time of theft determination. The work order system now allows for those evidence records and photographs to be loaded into the in-truck laptop and uploaded to a representative to determine what billing is needed. Rather than bill a retail customer directly, CEHE invoices the retail electric provider (REP), which, in turn, pays CEHE in full for the transmission and distribution invoice. CEHE collects its revenue even when the REP is unable to do so. It is the responsibility of the REP to bill and collect from its retail customers.
Algorithm Refinements
CEHE makes extensive use of the data captured by the advanced metering system, including alarms, alerts, usage data and transformer sensor data. Algorithms count certain events and patterns, and look for repetitive patterns and anomalies to identify suspect premises. In the future, the plan is to enrich that data with external sources such as weather information, county tax authority records and credit reports. All of CEHE’s algorithms have been developed internally, and there is no third-party software provider to run them. The following correlation events and algorithms are used:
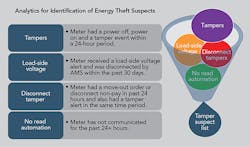
- A meter disconnected for nonpayment or move-out followed by any type of tampering event in the past 48 hours
- A remote disconnect followed by a load-side voltage event within 30 days
- A meter that has not communicated in the past 24 hours and has no other correlation event
- A power outage event followed by a removal alert within 24 hours, followed by a power-restore notification
- Usage that is 50% of the usage recorded in the same time frame in the prior year
- Usage that is 300% greater than in the previous month
- Load-profile shapes that mimic normal daylight/nighttime patterns; this pattern is a unique identifier of marijuana grow houses.
Additionally, CEHE identifies theft by partnering with local law enforcement agencies in a two-way conversation. Customers can report possible cases through a hotline phone number or on the corporate website. Field crews performing normal routine maintenance to the system also identify theft of service.
Ongoing Discoveries
Often CEHE is asked, “What have you learned?” While there is no one answer and learning is continuous, the utility has learned a few things:
- The advanced meters provide more data than originally expected.
- The data is only part of the story.
- Plenty of vendors are ready to offer software solutions.
- Most importantly, one could spend a tremendous amount of money trying to solve the problem, but there is a better way.
Theft-detection programs at CEHE continue to pay for themselves. On average, the utility investigates approximately 3,000 potential theft cases each month and realizes an approximately 50% to 60% truck roll success rate. CEHE believes an effort to reach a much higher truck roll success rate could cause many cases to be missed if the number of possible premises is limited to those that have a greater probability of actually finding theft of service.
CEHE and its predecessor utilities began implementing theft-detection programs more than 40 years ago, and the types of diversion and meter tampering continue to evolve. Thieves use different techniques and strategies to make the detection process an ongoing challenge. CEHE must change its analytic tactics constantly to adapt to these changing dynamics in the field.
The Score Model
CEHE envisions eventually using multiple algorithms to create a score, which will include not only the possible success rate but also the potential dollar value. The score model will have a self-learning component that takes in the results and modifies itself accordingly. CEHE’s current program uses a few transformer monitors, and the utility has had great results with data from those monitors pinpointing theft at a premise attached to the monitored transformer.
Field inspection programs also have been implemented with the goal of aligning customer records with field records. On occasion, a meter at one premise may have been moved to another location. The field inspection program enables CEHE to verify the correct location of a meter and make the appropriate corrections within the customer information system and ensure the billing records, meter records and premises records all are aligned and accurate.
Thieves bypassing the meter as a method of theft are more difficult to pinpoint because the advanced meter does not provide any alarms or alerts. CEHE also has found, on occasion, electromechanical meters in the field that were never entered into the customer information system. The only way to find such meters is by using a focused field and meter inspection program. Data integrity, or the lack thereof, has a direct impact on the effectiveness of the algorithms used to detect potential theft and ensure the integrity of the revenue stream.
Although it takes an aggressive approach, at this point, CEHE does not focus on prosecuting individuals for energy theft. Use of the legal system can increase cost that is greater than the recovery of revenue. However, in some cases, the potential for reduced losses in the future — when word of mouth spreads, the utility is committed to stopping the theft of service — could offset the cost of legal action. Electricity theft is punishable by jail time, fines or both. Many perpetrators do not realize tampering with live electricity is not only illegal but dangerous, and could result in a fire or electrocution.
Extensive measures are taken to prevent electricity theft, and the advanced meters are helping to do so even faster.
It Takes a Team
CEHE employs a limited staff to identify theft and recover lost revenue. Its field operations/revenue protection department, part of its electric market operations group, is responsible for meeting the utility’s theft-detection goals and ensuring regulatory compliance by adhering to billing and evidentiary record rules. The group has overall accountability for the methods and results of CEHE’s theft-detection program.
Currently, the field operations/revenue protection department is staffed with 30 dedicated employees, including management, investigators and billing representatives. The investigators have the primary responsibility for investigating and mitigating theft situations. The other resources handle activities that follow up with billing, evidence record keeping and notification.
The group works hand in hand with CenterPoint Energy’s corporate analytics data services group to develop the analytical algorithms and scoring tools. The specially trained investigators respond to the investigation orders and all reports of theft that come in through the hotline or website; coordinate with local law enforcement; and determine the best billing methodology to use in calculating the cost of labor and material. All of these described components work together to make CEHE a top performer in the arena of utility theft detection.
Susan Neel ([email protected]) is the senior director of electric market operations and field operations at CenterPoint Energy Houston Electric. Her responsibility includes revenue protection, maps and records, electronic transactions management, credit and risk management, competitive retailer relations, business process and system requirement designs, and field services. She has 37 years of experience in the operations of CenterPoint Energy from the meter to cash and all aspects that touch the customer and the Texas retail market.