A homeowner is away for the day celebrating Independence Day with the family. A thief discovers an unlocked door to their house. He lets himself in and pilfers items that will not raise immediate suspicion. Before the homeowner comes home, the intruder sequesters himself in the utility room. For months thereafter, the intruder continues stealing valuables, bit by bit. One day, just before Christmas, the outdoor lights and heater the thief has been using overloads and trips a breaker. While checking the breaker panel in the utility room, the homeowner discovers the thief who has been lurking in his home for almost six months.
It is a bizarre scenario, but in the world of cyber intrusion, it is not; it is the norm. The amount of time that elapses between a cybersecurity breach and its detection is, on average, 205 days — a number that gives security experts cause for concern. Expert opinions about this situation vary from it being embarrassing to being obscene. The good news is that detection of a breach is already improving. In 2013, cyberattackers had an average of 229 days before detection. The bad news is that it is a lot longer than that in many cases.
It Is Going to Happen
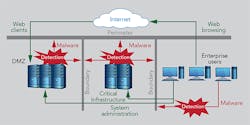
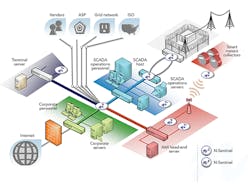
In a highly decentralized network environment with multiple entry points, hackers have many opportunities to breach security and gain unauthorized access to the system, data and controls. The sprawling Internet of Things, in addition to the vast volume of data generated and shared by connected devices, further jeopardizes the security of private networks. At risk are utilities’ financial assets, operational continuity, equipment protection, customer privacy, information and data security, as well as the reputation of the organization.
The large number of potentially vulnerable access points means a breach of perimeter security is more than just a theoretical event — it is a virtual reality. For most organizations, including electric utilities, a breach is only a matter of time. When compromise occurs, what happens next can largely determine the scope of damage, whether limiting or enabling it. Quickly identifying the intrusion is critical. Given enough time inside a house or network, even the most incompetent thief will rob the owner blind, with likely lasting damage.
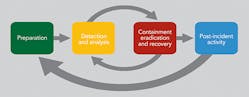
Detection is the key step between prevention and corrective action. It is not enough to put up a firewall, install antivirus software or patch the system. Organizations need to have ongoing 24/7 monitoring.
It Has Been Happening
Across the globe, the number and severity of cyberattacks is growing, including those aimed at industrial targets. In 2010, the Stuxnet worm infected an Iranian nuclear enrichment facility, most likely by way of an infected USB flash drive, and destroyed an estimated 1,000 centrifuges. The attack issued commands that caused the machines literally to spin out of control. There is broad agreement the U.S. and Israel were responsible for the attack, which many experts consider to be the first documented and significant act of cyberwarfare.
Retail giant Target has reported expenses related to the cyber theft of customer credit card information totaled US$250 million in 2013 and 2014. A portion of those losses were offset by insurance claims.
In late 2014, Germany’s Federal Office for Information Security reported hackers had gained control of a German steel mill’s control system, preventing a blast furnace from shutting down and causing massive damage.
According to Wired magazine, “Attackers gained access to the steel mill through the plant’s business network, then successfully worked their way into production networks to access systems controlling plant equipment. The attackers infiltrated the corporate network using a spear-phishing attack. Once the attackers got a foothold on one system, they were able to explore the company’s networks, eventually compromising a multitude of systems, including industrial components on the production network.”
Malware has infiltrated equipment at a nuclear power station and other generation facilities, resulting in start-up delays. Other targets include railway systems, water facilities and car washes. Malicious software has been found on servers and even computer equipment shipped from manufacturers. And a pair of cybersecurity researchers recently discovered network vulnerabilities in the Tesla Model S that allowed them to turn off the engine of the electric car while someone else was driving it.
The Kill Chain
Hackers typically follow a four-step plan for breaching cyber defenses and compromising organizations’ assets, which cybersecurity professionals call the “kill chain”:
• Conduct reconnaissance. The attacker analyzes the intended victim to identify a way to get in and see what they want to get once they penetrate the network.
• Establish a foothold. The attacker gains control of a single computer inside the perimeter, generally a server or a personal computer, and loads tools onto it that enable remote control.
• Move laterally and gain privileges. The attacker moves around the network to get closer to computers he or she wants to access and obtains privileged credentials to access them.
• Accomplish the mission. The attacker accomplishes the mission: stealing data (confidentiality), changing data (integrity) or destroying data (availability).
Accomplished hackers are hard to detect. They are found by looking for disturbances in the cyber environment. It is like looking for the footprints of an invisible man. One familiar with the contours of the undisturbed network landscape knows when someone has been there. Knowing what normal looks like is as important as detecting abnormal.
A Measure of the Threat
Forward-thinking utility leaders are preparing today for tomorrow’s cyberattacks. They ignore yesterday’s good fortune. To date, hackers have not taken down an electric utility or disrupted the grid — yet.
That could be less a matter of impenetrable network defenses and more a case of insufficiently motivated hackers. This could change if attackers get to the point of wanting to use cyberattacks for ransom or geopolitical advantage. Indeed, there have been many cases of hackers taking data hostage and demanding ransom payments to release it. Eventually, somebody may say, “If you want your power back on, you have to pay.” Stealth is the hacker’s credo.
During a demonstration of an N-Dimension Solutions cybersecurity monitoring service this summer, the firm’s cybersecurity experts identified undetected malware on the network of a participating electric utility, a cooperative in the eastern United States with a service territory of just under 1,000 sq miles (2,590 sq km).
N-Dimension is a managed security service provider with expertise in protecting smart energy networks from cyber threats. The company has seen quite a few incidents lately of command and control channels, things like resident malware at utilities. It has seen communication back and forth out of the networks, which gives hackers the ability to pull information out of a network, install new malware and spread it to different machines. Many times hackers will use encrypted channels so it is hard to tell what they get.
In the past few years, several electric utilities have come under attack:
• In 2012, a Midwestern utility that opted out of installing a cyber defense system suffered a cyber intrusion that has resulted in losses of more than $2 million. Multiple lawsuits are pending.
• In 2013, hackers penetrated the network defenses of a Northeast investor-owned utility and stole more than one-third of its customers’ records before the security system detected and blocked the attack.
• In 2014, criminals hacked a Southern utility, stealing W-2 tax form information that was then used to file false tax returns.
• Also in 2014, hackers breached the cybersecurity of a Midwestern utility and took control of its supervisory control and data acquisition system.
A Threat from Within
One of the biggest cybersecurity threat vectors is an organization’s own workforce. One of the best electric utility IT departments in the U.S. was compromised by someone who brought in a USB drive with their child’s school Christmas pageant on it.
Compounding the challenge, many organizations lack the expertise to mount a rigorous defense against what, at times, seems like legions of hackers bent on finding a way to infiltrate their networks. There are a lot of good cybersecurity tools available, the problem is there are not a lot of good cyber-security experts.
The key strategy is monitoring, knowing what is going on and improving security every day. Simply gathering data is not enough. Like many complex endeavors, cybersecurity is an art and a science, where behavior and techniques matter more than specific pieces of code. One should be probing the network all the time to see what is new and what has happened since it was last done. Part of it is learning cybersecurity, but another part is learning what is regular for the network.
The Essence Project
In March 2015, 10 electric utilities took part in a demonstration project where they were the target of 8 million cyberattacks. For these eight cooperatives and two municipals, the hits occurred every 2.6 seconds on average. Bots (a web robot) delivered the vast majority of the attacks, the cyber equivalent of a burglar jiggling the doorknob to see if the door is open.
Given the volume, tenacity and mutability of attacks and attackers, architects of utility cybersecurity strategies would do well to adopt the principle of continuous improvement. The principle is a process and a culture, not a technology checklist. One size does not fit all.
The Essence project is a research effort funded by the U.S. Department of Energy and includes partners NRECA, Cigital, Pacific Northwest National Lab and Carnegie Mellon University. The project addresses five approaches to cybersecurity:
• Chase the bad guys, largely a function of defense and law enforcement agencies, including the FBI, Defense Department and Department of Homeland Security.
• Build walls around networks and block access.
• Harden the interior of networks by designing applications that are less vulnerable.
• Segment system architecture the way a seagoing freighter compartmentalizes its hull. If something breaks, the entire system does not crash.
• React quickly when something goes wrong.
The first four have been improved. However, the biggest potential is to cut down the 205 days it takes to detect a security breach. What if this number were reduced to one day or less? The belief is cybersecurity systems have to break out of the narrow domain of just looking at the network components and begin looking at the totality of utility operations.
The idea behind Essence is to look at all utility network traffic and analyze it for anomalies that might indicate a cyber breach. Essence also can monitor network traffic based on a set of utility-specific rules. For example, if two devices or servers that should not communicate with each other suddenly start exchanging messages, Essence can isolate that part of the network until the problem is resolved.
Essence is an open platform, which means anyone will be able to write applications that run on Essence. This opens up possibilities for many different approaches to improving
cybersecurity, all operating off the same framework. The single greatest area of importance in contemporary cybersecurity is rapid reaction. The idea is to detect early and marshal assets to cauterize the wound right away so that no more damage is done.
Acknowledgement
The authors thank Scott Dinnage of N-Dimension for his contributions to this article as well as for the key role that he has played in the entire project. Also, Maurice Martin, who was with NRECA during the project, contributed substantially to the article.
Craig Miller ([email protected]) is the chief scientist of the National Rural Electric Cooperative Association. He oversees a broad research portfolio and personally leads projects in several areas, including cybersecurity and advanced utility architecture. His current focus is reactive approaches to cybersecurity as an effective complement to traditional preventive methods such as firewalls and advanced grid control architecture for agile operations. In 1997, he received a gold medal from the Smithsonian Institution for a “heroic achievement in information technology.”
Gib Sorebo ([email protected]) is a chief cybersecurity technologist for Leidos, where he assists government- and private-sector organizations in complying with legal and regulatory requirements, and addressing cybersecurity risks. Sorebo has been working in the information technology industry for more than 23 years. He oversees and coordinates cybersecurity activities within the energy and other commercial sectors. He recently coauthored a book on smart grid security.